
By Uddave Jajoo
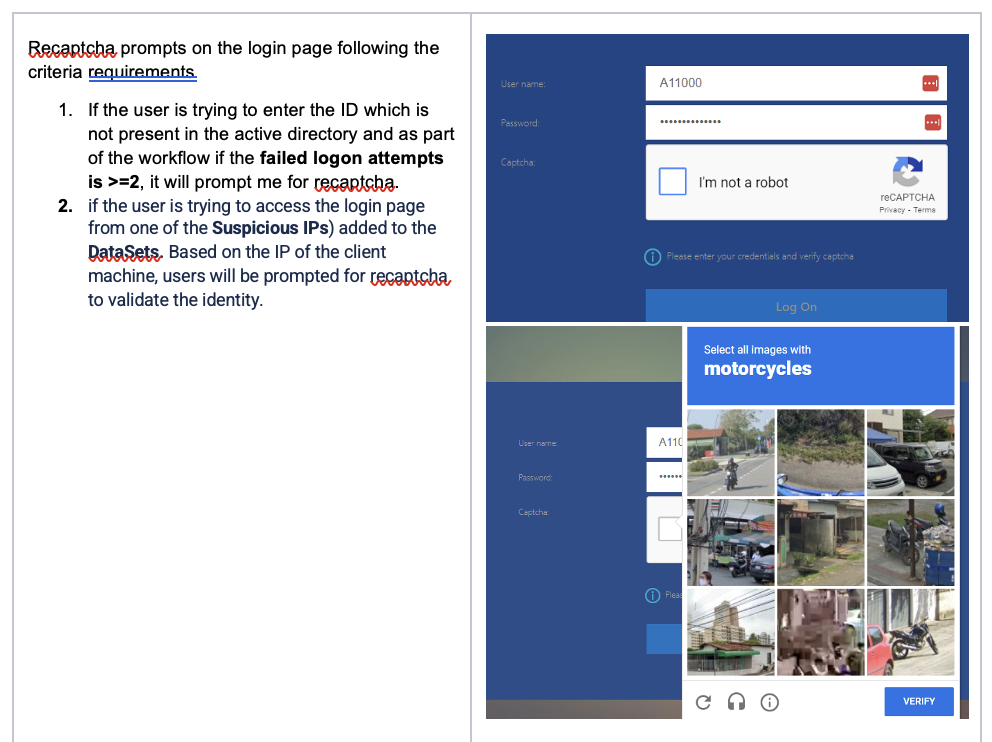
Recently encountered an issue with the logon spoofing attacks on our external gateway appliance, which triggered the need to have set up an advanced authentication mechanism using recaptcha solution. I started doing my research with this, and had to implement something which could be helpful in reducing the number of attacks and not impacting end user experience.
I came across several different articles on the web, then later consolidated all the different approaches and prepared this one solution.
For this recaptcha solution I have utilized google recaptcha service to validate the user response and setup authentication policies to validate the user identity and response.
In this blog article I am highlighting how effectively google recaptcha could be configured within your access layer to monitor the bad/malicious user accounts and restrict them to access your website.
- How To Setup reCaptcha site on Google
- Register the domain on the URL
- Add domains and add owners to the site
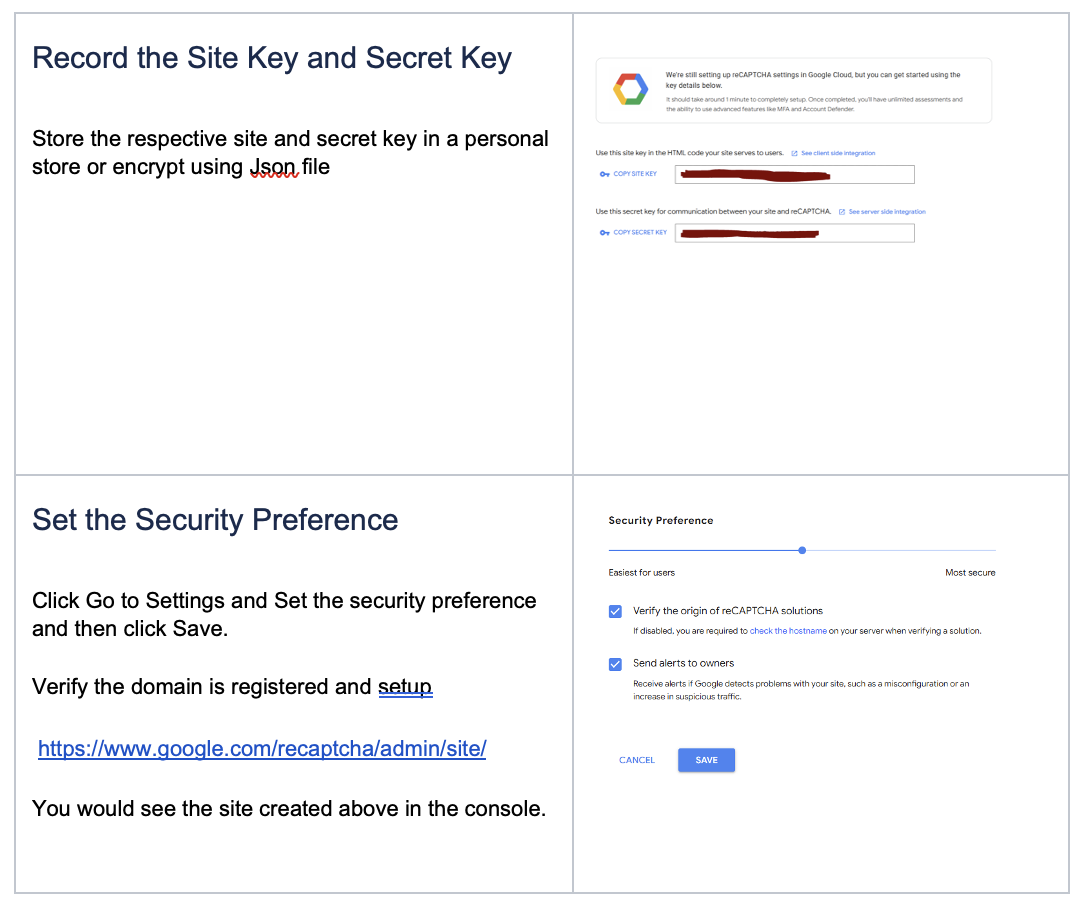
- Record the Site Key and Secret Key
- Set the Security Preference
- Verify the domain is registered and setup
- Add reCaptcha Authentication Policies On NetScaler
- Bot Protection
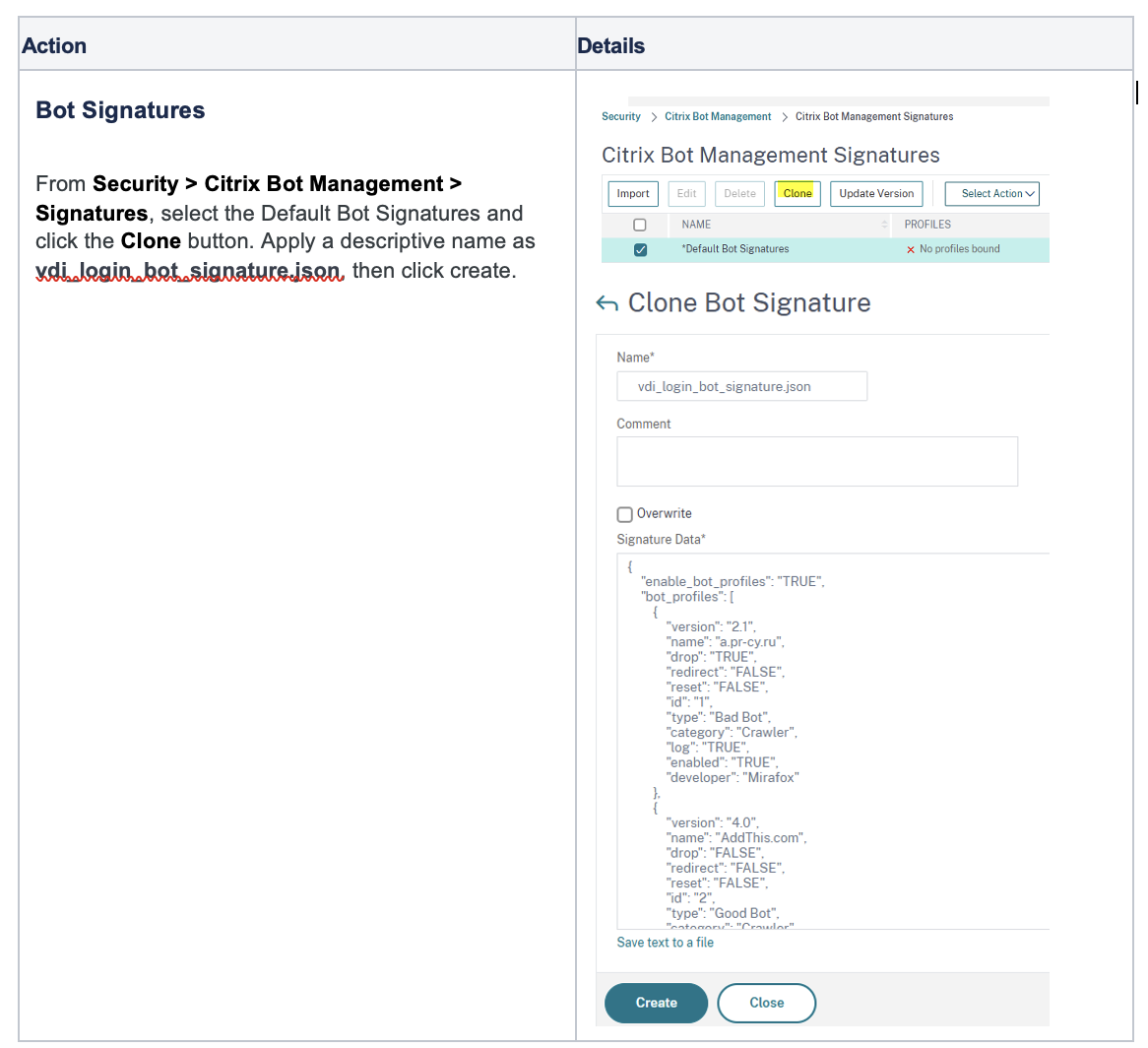
- Bot Signatures
- Create a Bot Management Profile and Policy
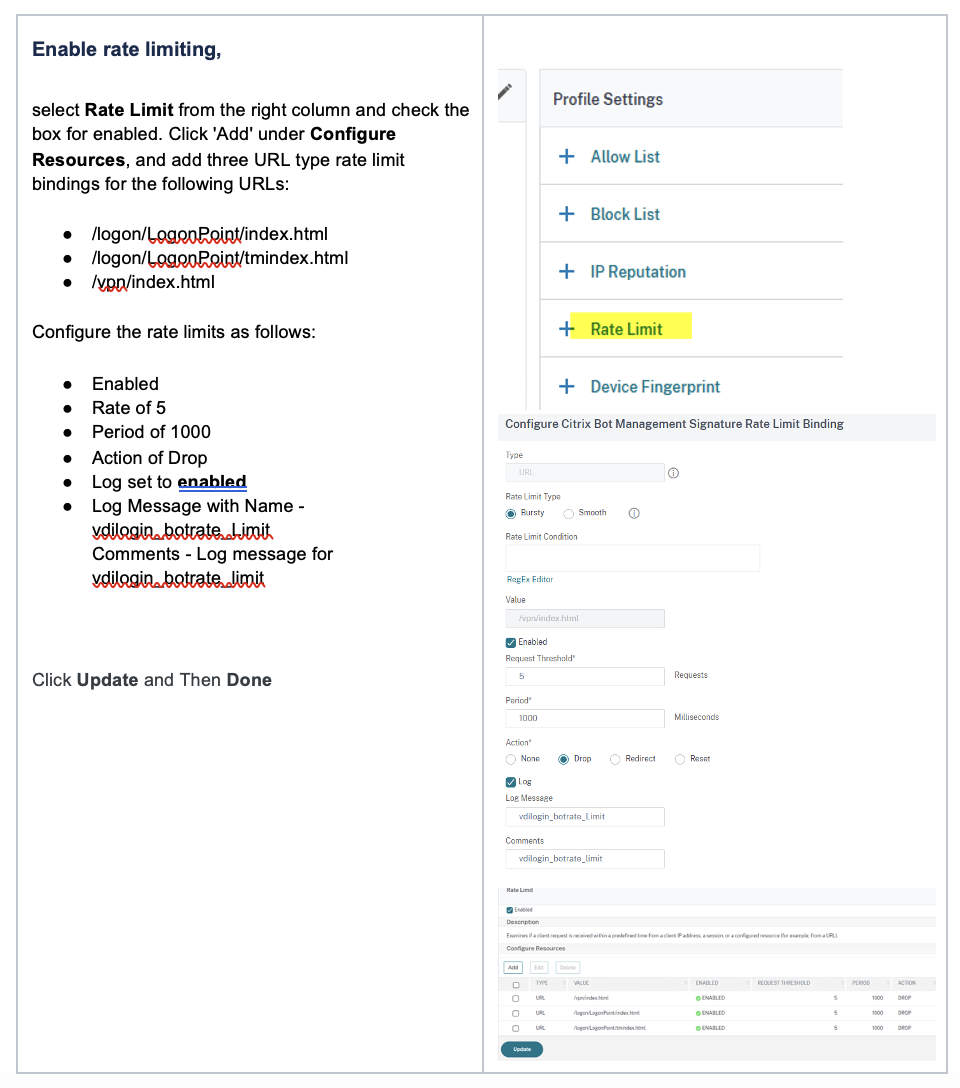
- Enable rate limiting,
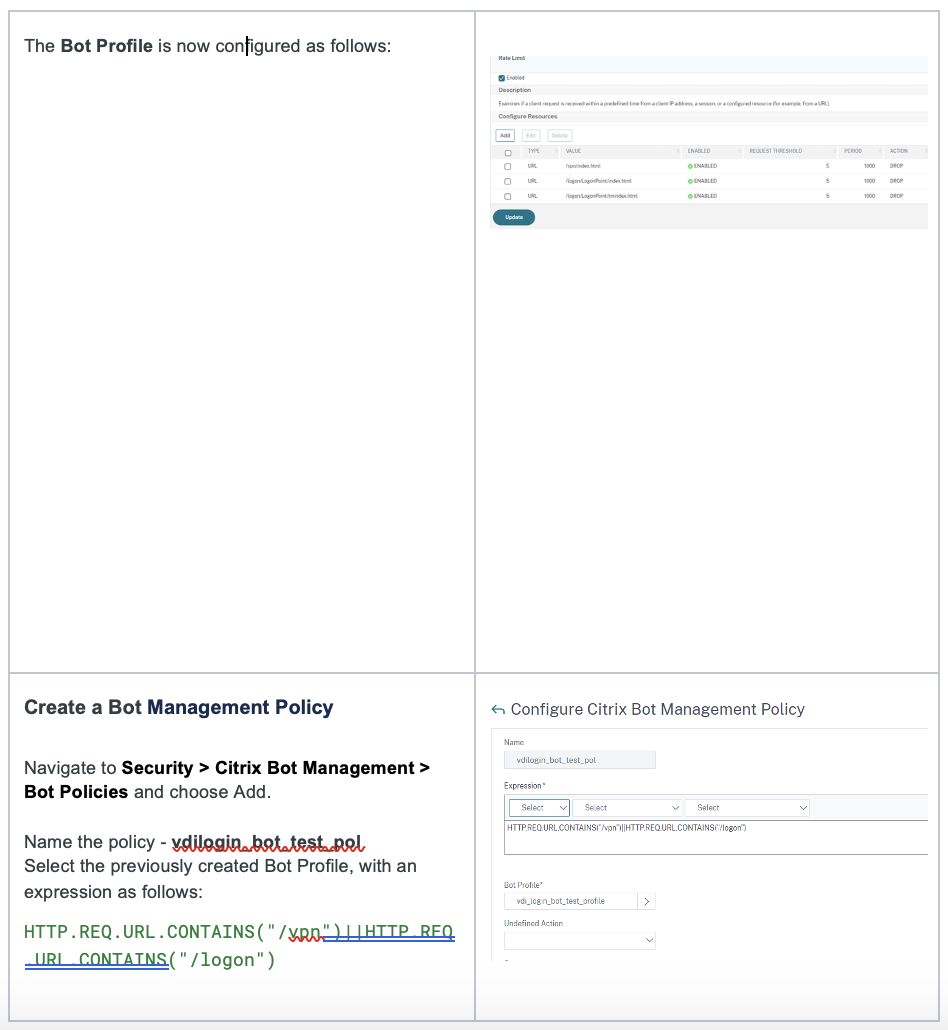
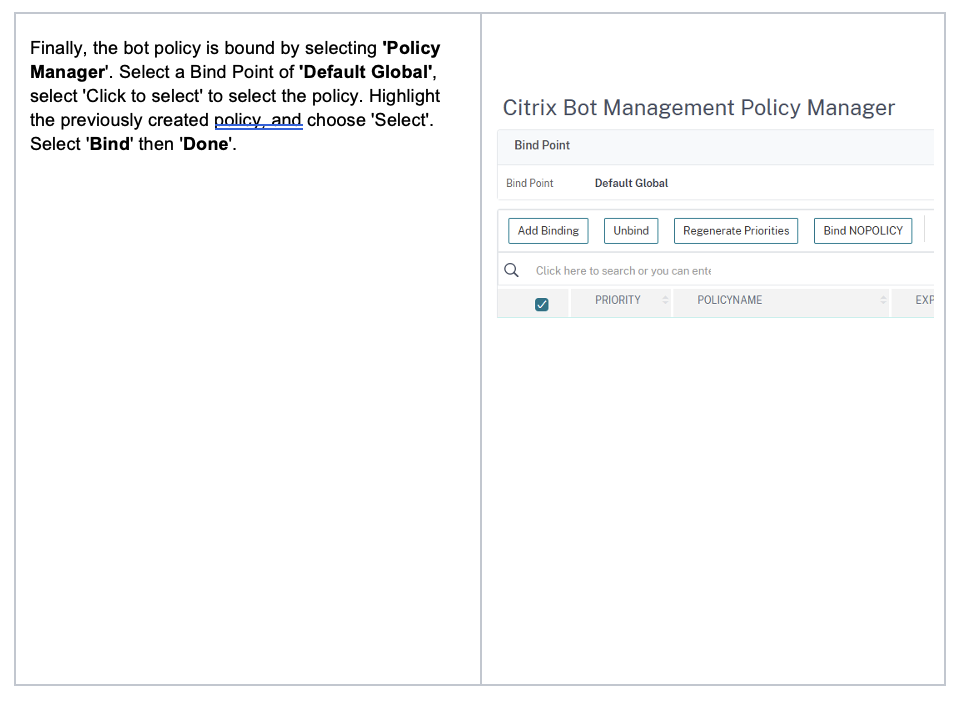
- Create a Bot Management Policy
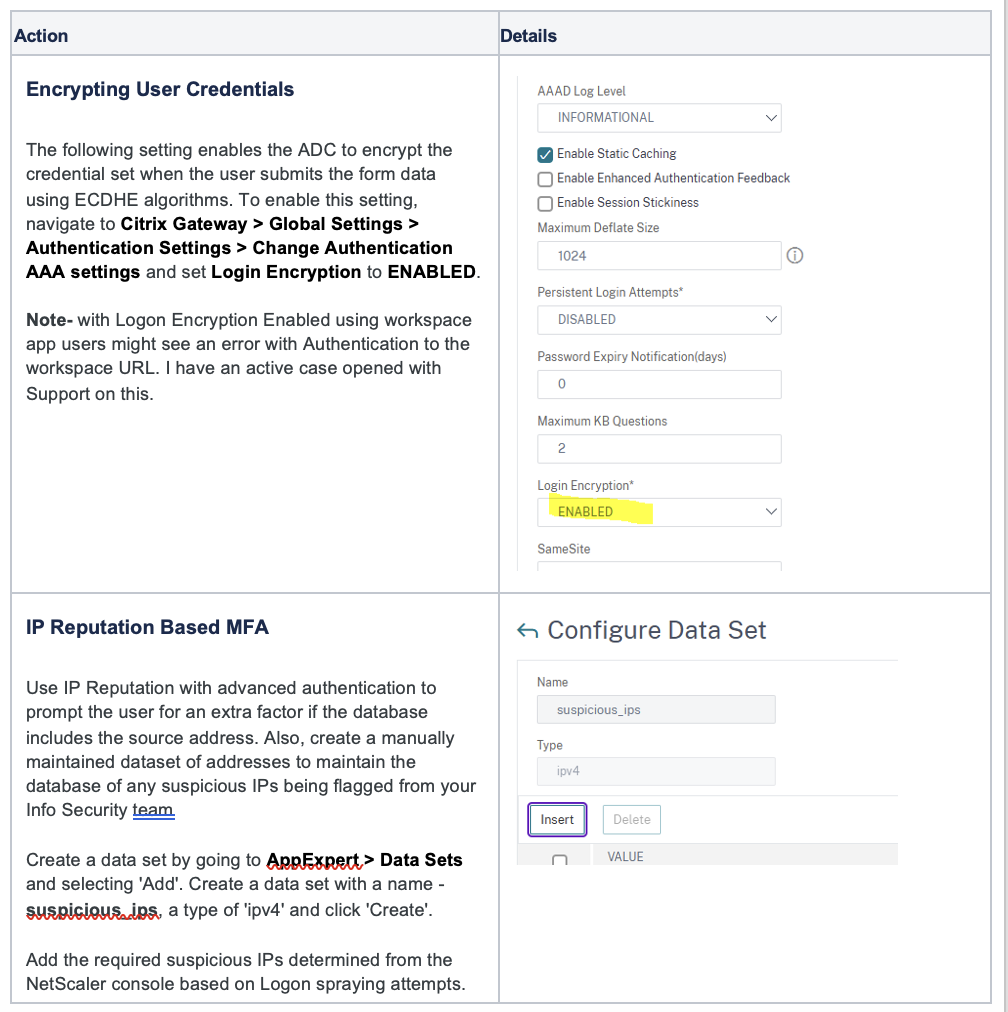
- Advanced Authentication Settings
- Encrypting User Credentials
- IP Reputation Based MFA
- Create Google reCaptcha Login Schema/Action/Policy/Policy Label
- Failed Logon Attempts Policy
- Bot Protection
- Add Authentication Policies to Authentication vServer
- Verify Re-captcha response to Google Server
- Additional Mitigation Steps
How to set up ReCaptcha:
a. )Register the domain on this URL – https://www.google.com/recaptcha/admin/create#list
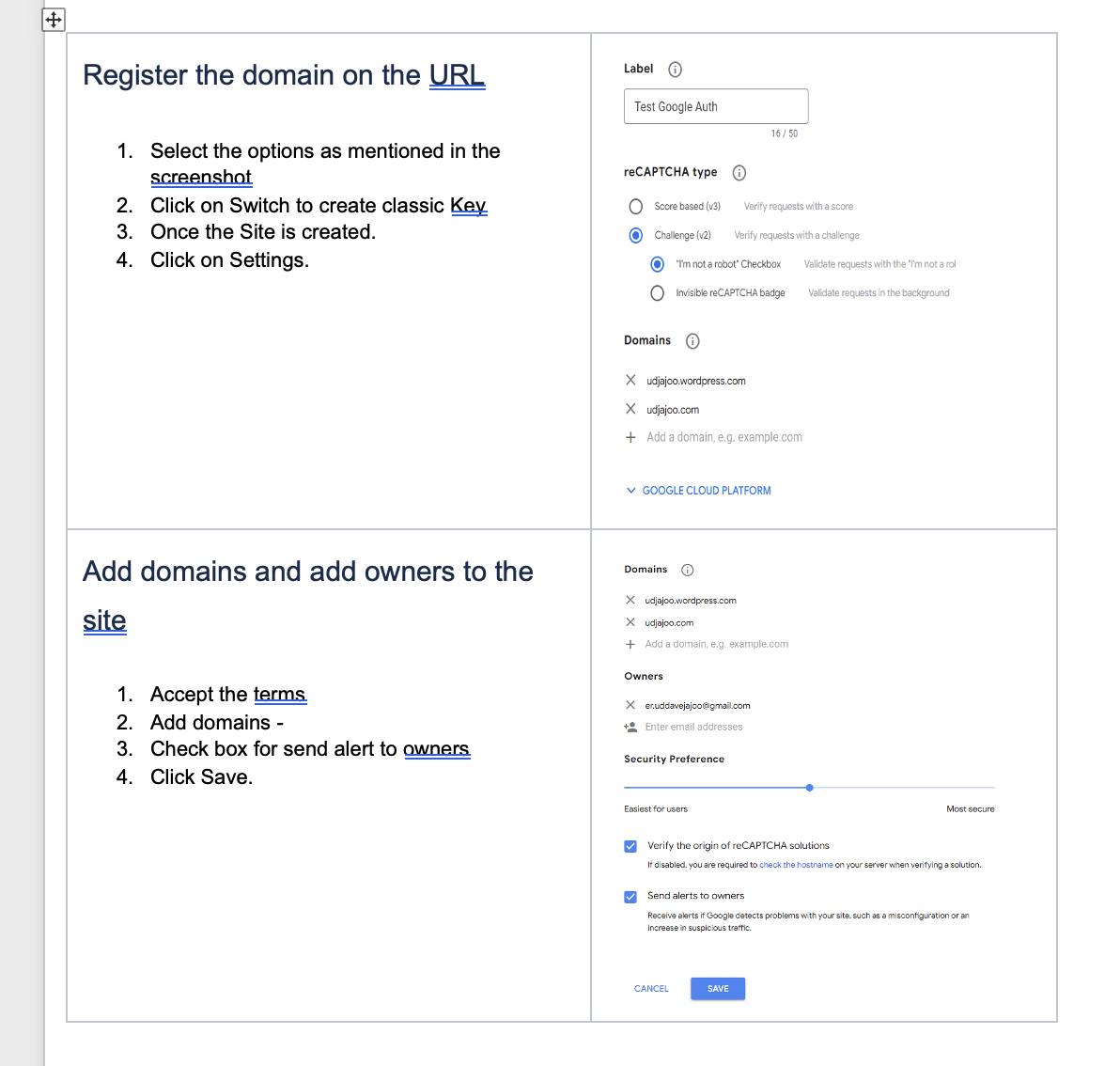
2. Add reCaptcha Authentication Policies On NetScaler
a.) Bot Protection
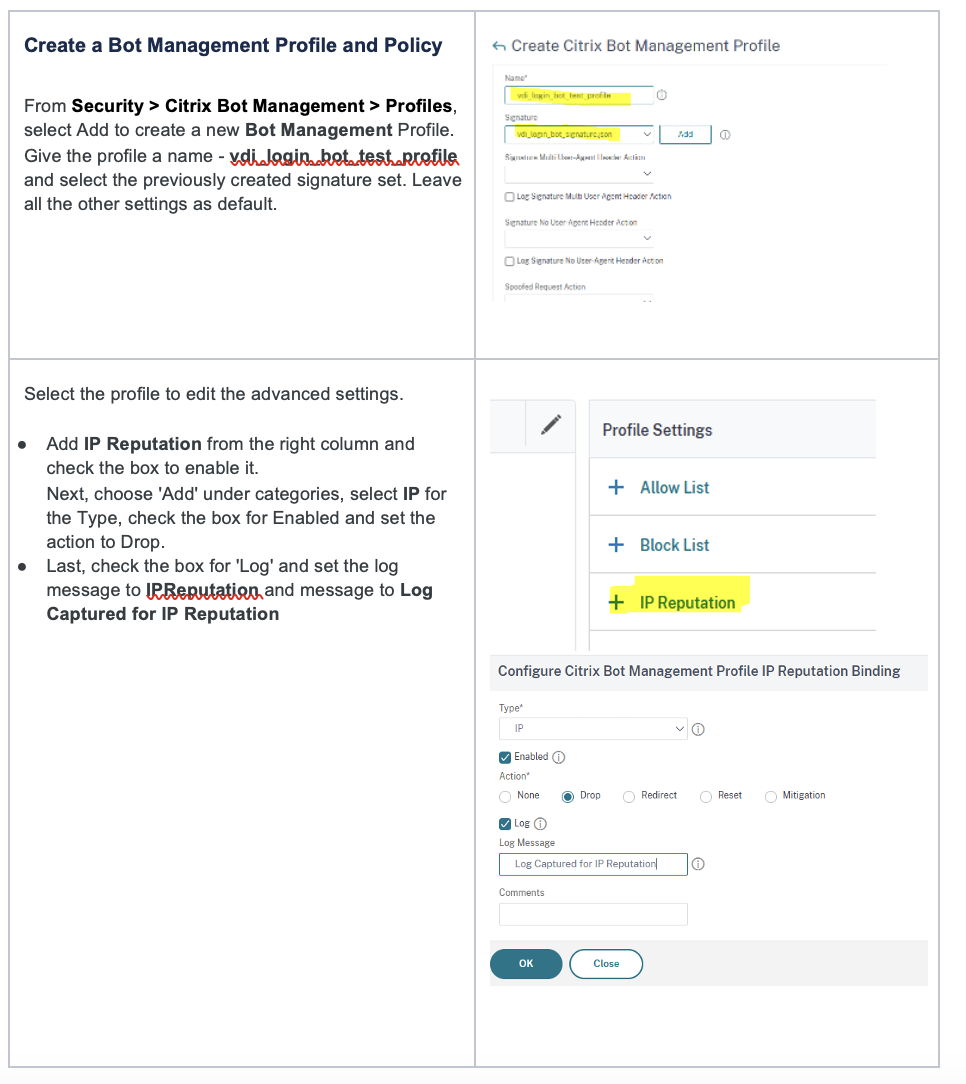
b.) Advanced Authentication Settings
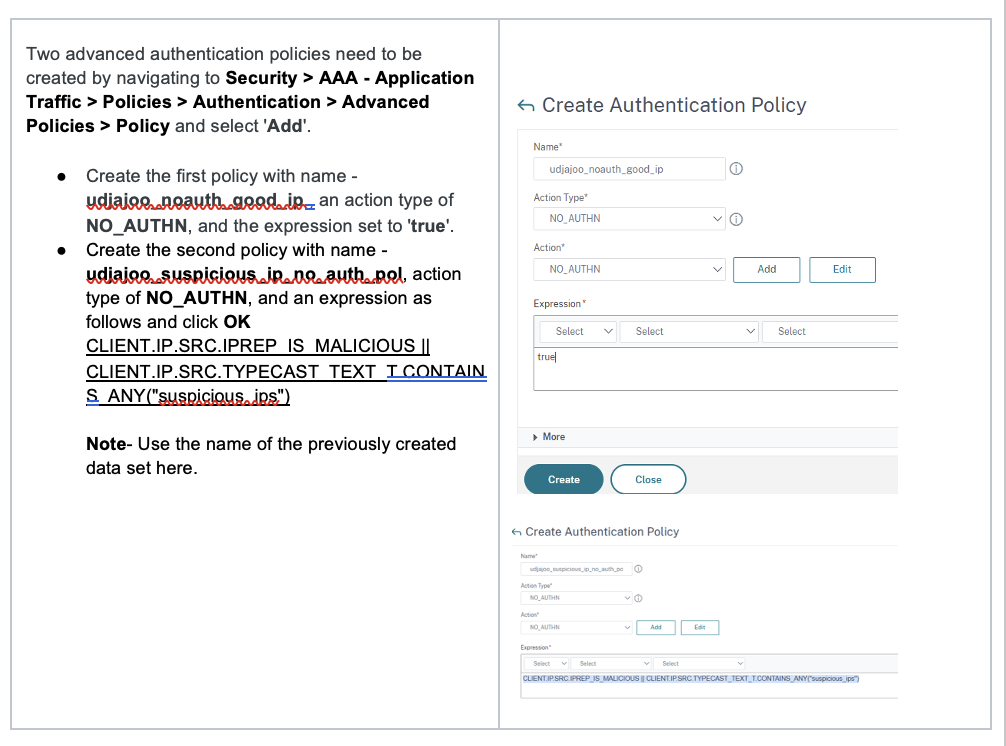
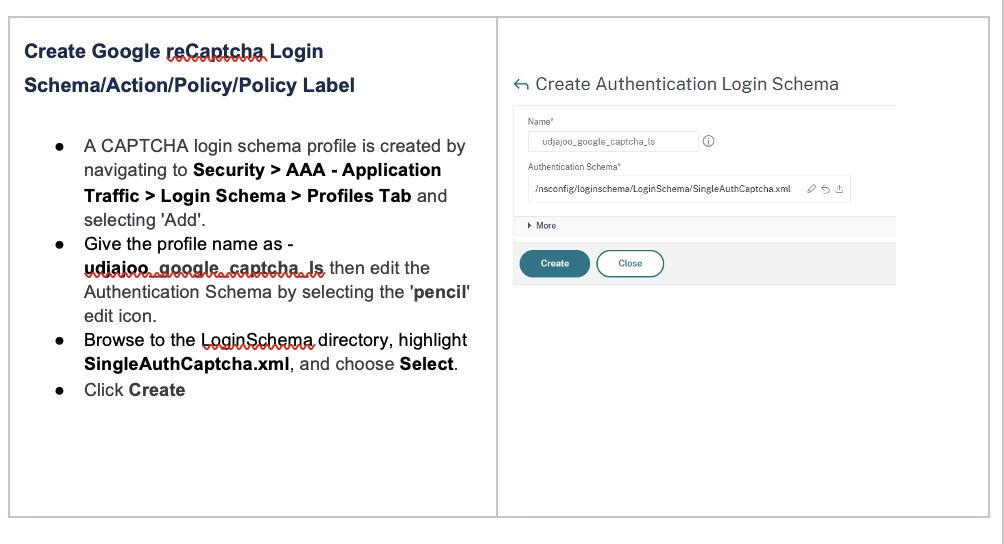
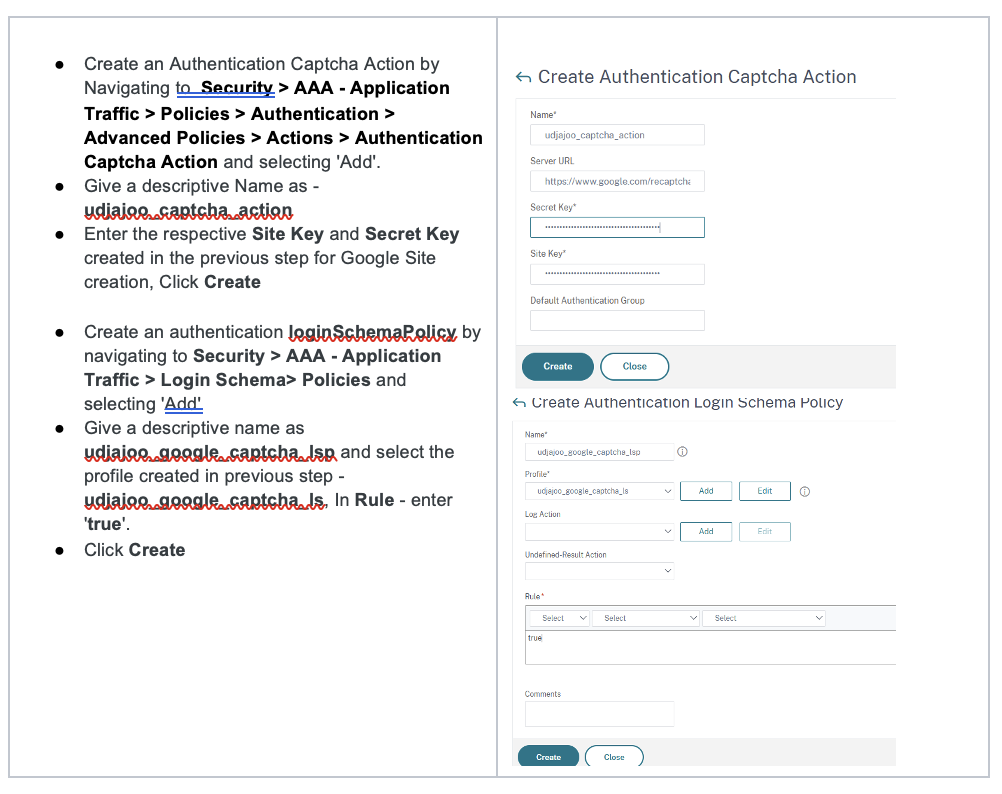
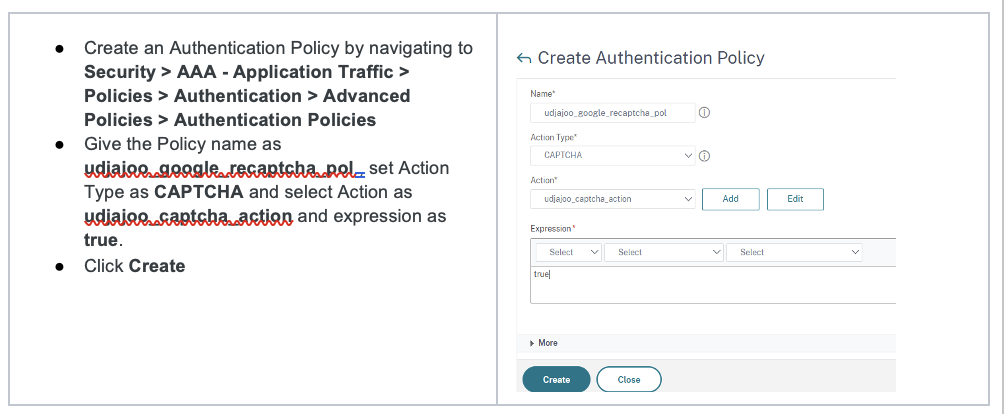
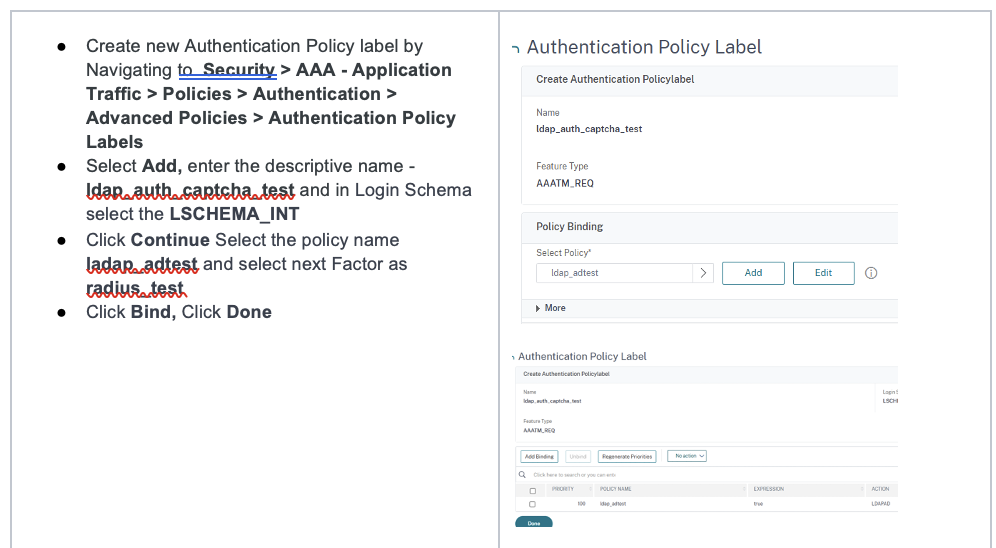
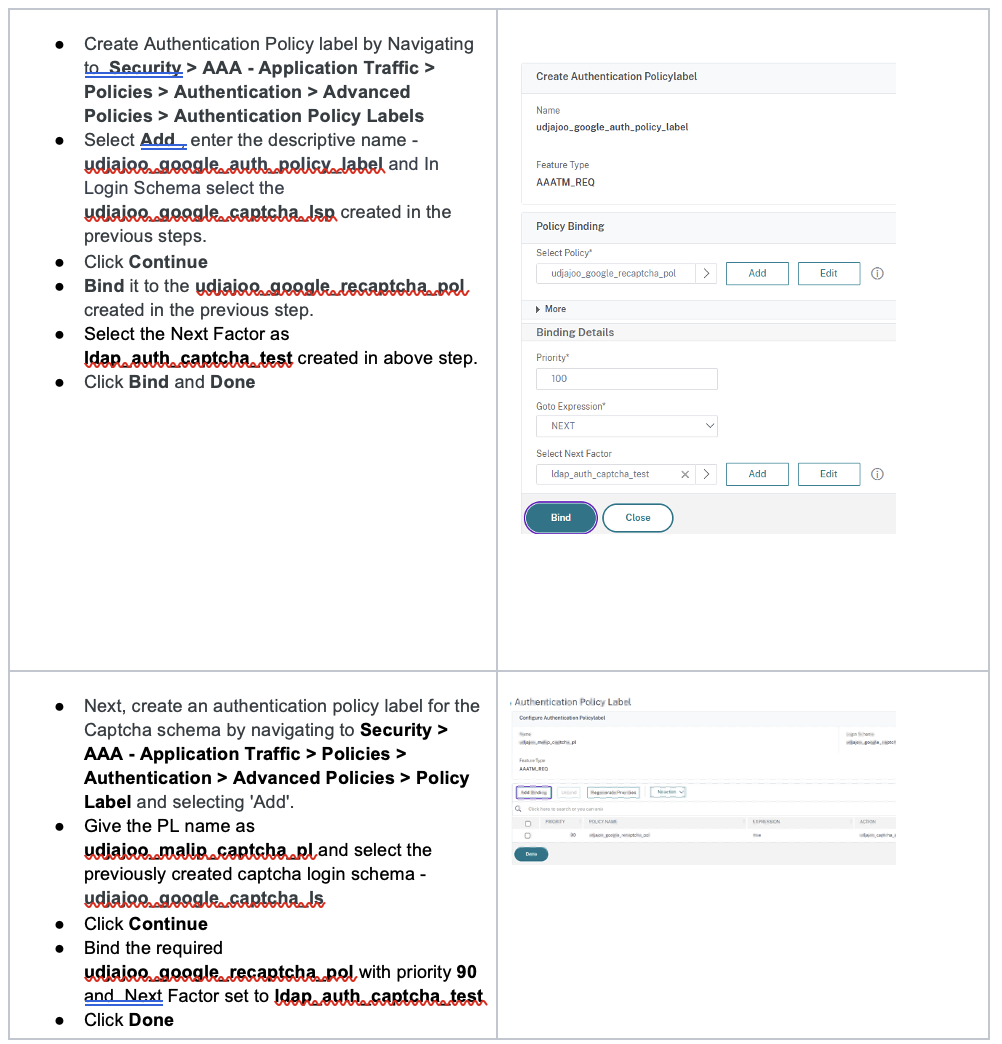
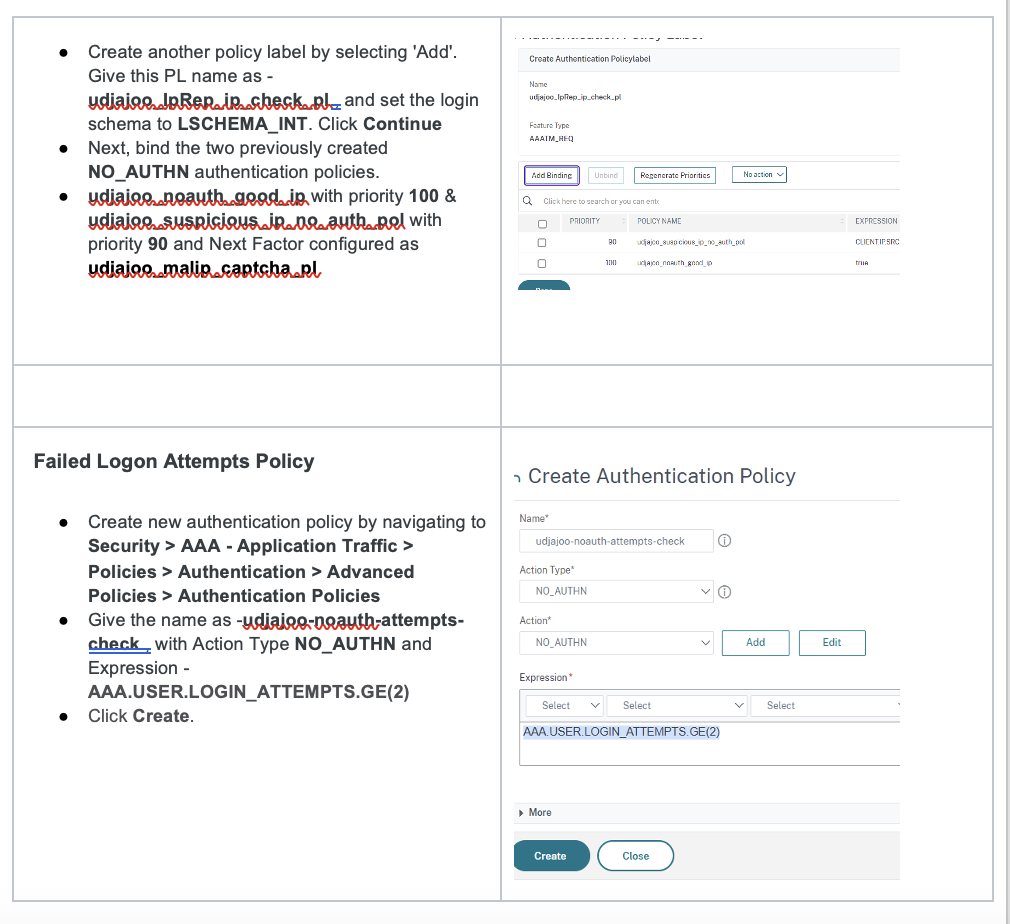
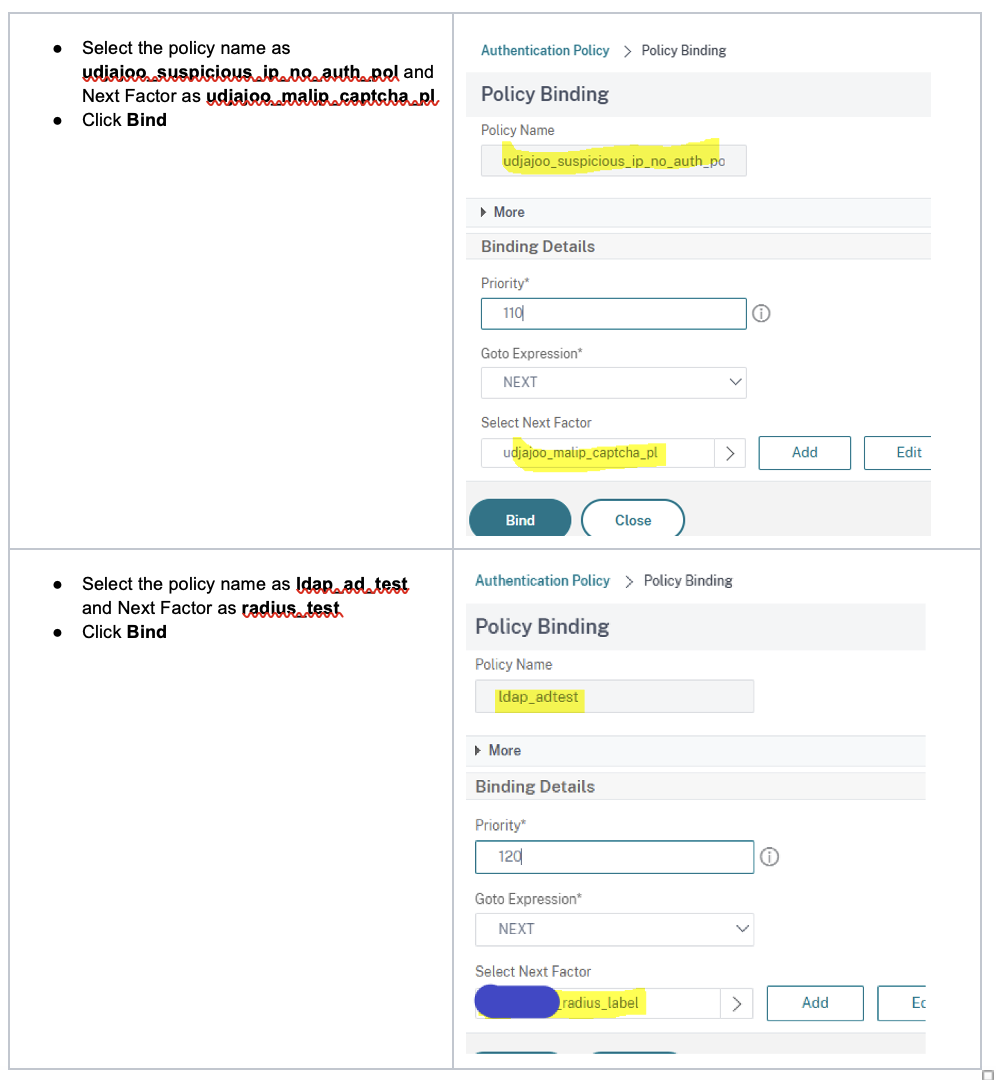
Add Authentication Policies to Authentication vServer
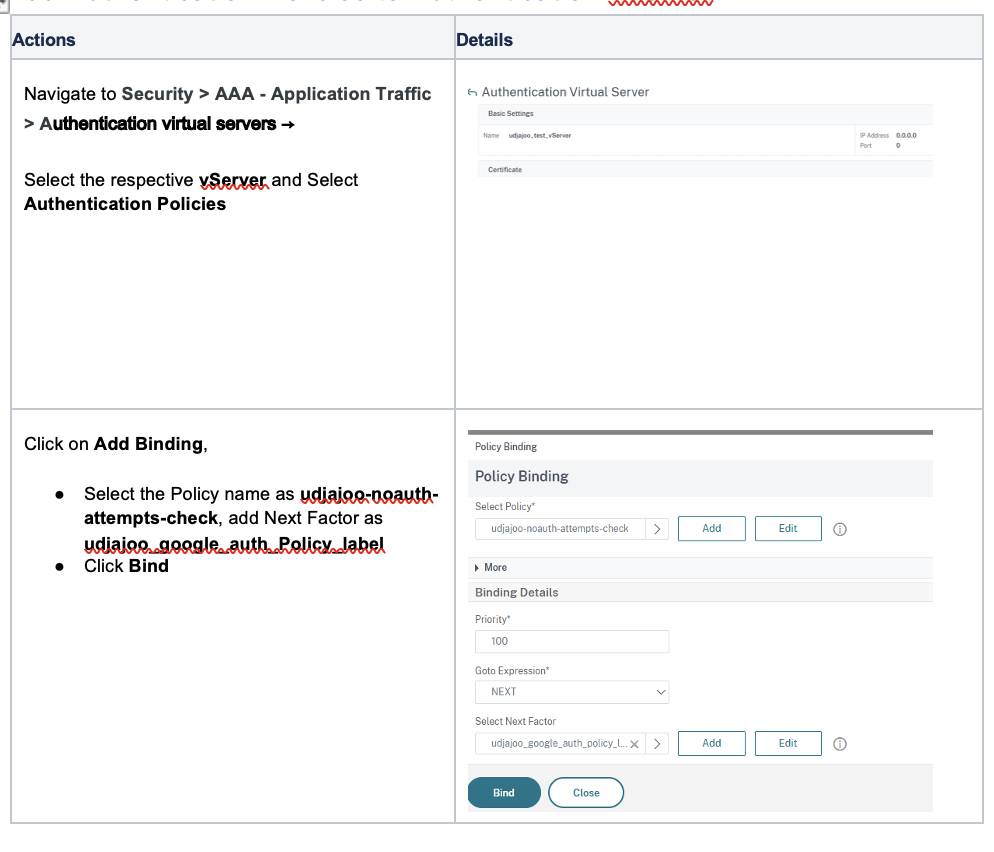
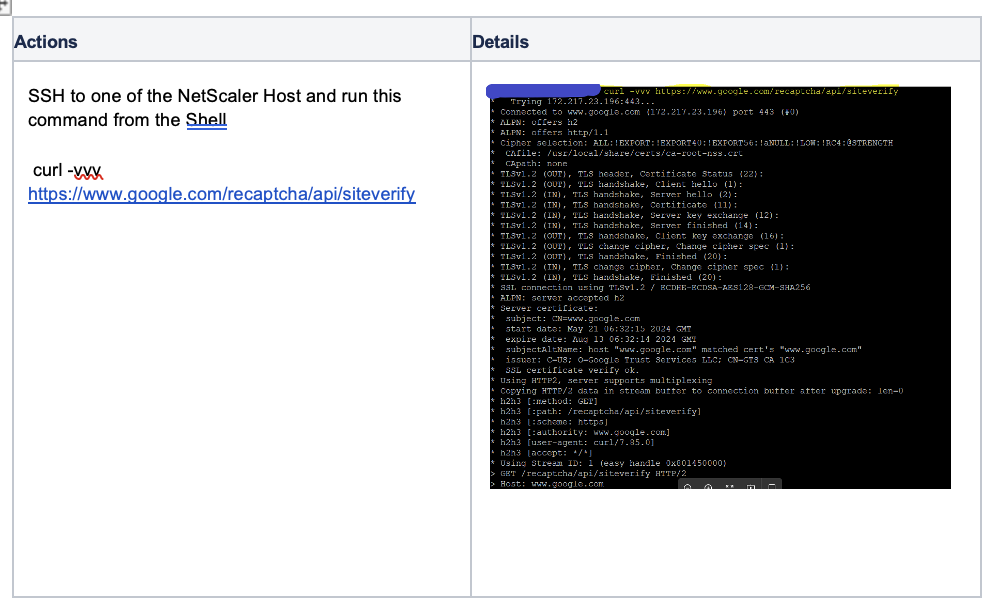
4. Verify Re-captcha response to Google Server
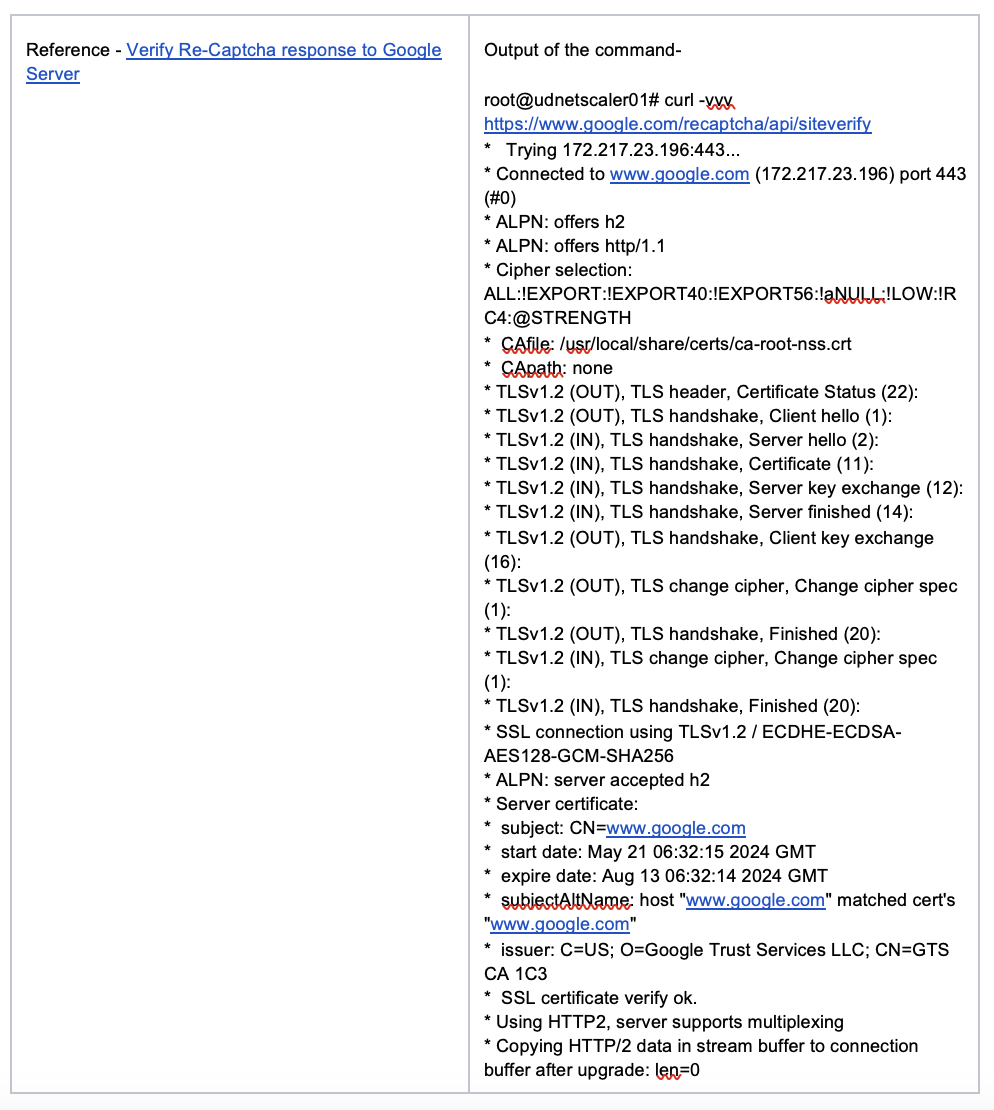
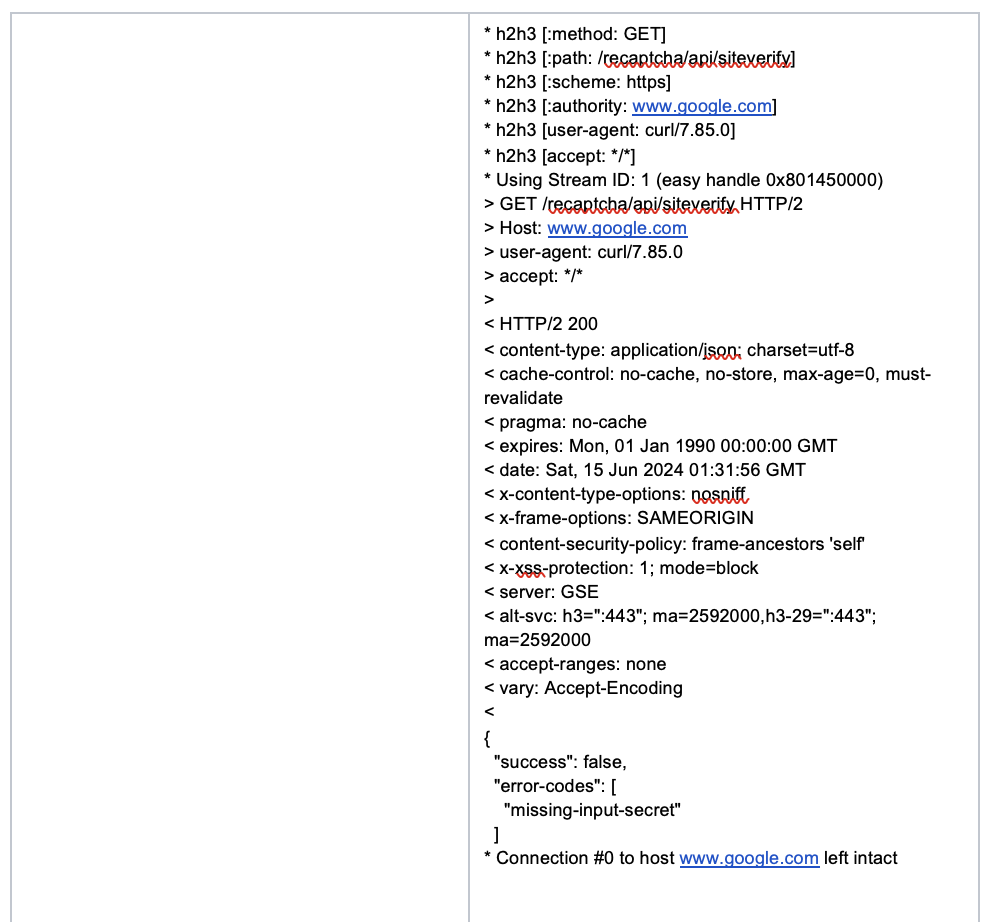
5. Additional Mitigation Steps – Citrix Article
● Ensure that multi-factor authentication is enabled for Gateway and the MFA verification factor is configured before the LDAP factor.
● Create a responder policy to allow requests only for desired FQDN, as attacks are frequently targeting IP addresses rather than Gateway FQDNs. Create the following responder policy:
- add responder policy IP_Block “HTTP.REQ.HOSTNAME.EQ(\”\”).NOT” DROP
- bind vpn vserver Gateway_vServer -policy IP_Block -priority 100
● Create a responder policy to block the following end points if not utilizing historic pre-nFactor basic/classic authentication:
● /cgi/login
● /p/u/doAuthentication.do
● /p/u/getAuthenticationRequirements.do
● Here are the responder policies that need to be created:
- add policy patset patset_block_urls
- bind policy patset patset_block_urls “/cgi/login”
- bind policy patset patset_block_urls “/p/u/doAuthentication.do”
- bind policy patset patset_block_urls “/p/u/getAuthenticationRequirements.do”
● add responder policy policy_block_urls
“HTTP.REQ.URL.SET_TEXT_MODE(IGNORECASE).CONTAINS_ANY(\”patset_block_urls\”)” DROP
- bind vpn vserver Gateway_vServer_name -policy policy_block_urls -priority 100
-gotoPriorityExpression END -type AAA_REQUEST
● Enable IP reputation to automatically block requests from known malicious IP addresses, reducing attack volume. On NetScaler CLI, use the following commands to enable IP reputation:
- enable feature reputation
- add responder policy policy_block_malicious_ip CLIENT.IP.SRC.IPREP_IS_MALICIOUS” DROP
- bind vpn vserver Gateway_vServer_name -policy policy_block_malicious_ip -priority 50
- gotoPriorityExpression END -type AAA_REQUEST
Reference Links –
Supporting reCaptcha with NetScaler nFactor
Bot Detection | NetScaler 14.1
reCaptcha configuration for nFactor authentication
Password spraying attacks on NetScaler/NetScaler Gateway – December 2024
